Era switch to Pythagoras
Era switch to Pythagoras
We have introduced the Pythagoras era in the Mithril networks. The switch to Pythagoras is a significant milestone that brings new features and improvements to the Mithril protocol.
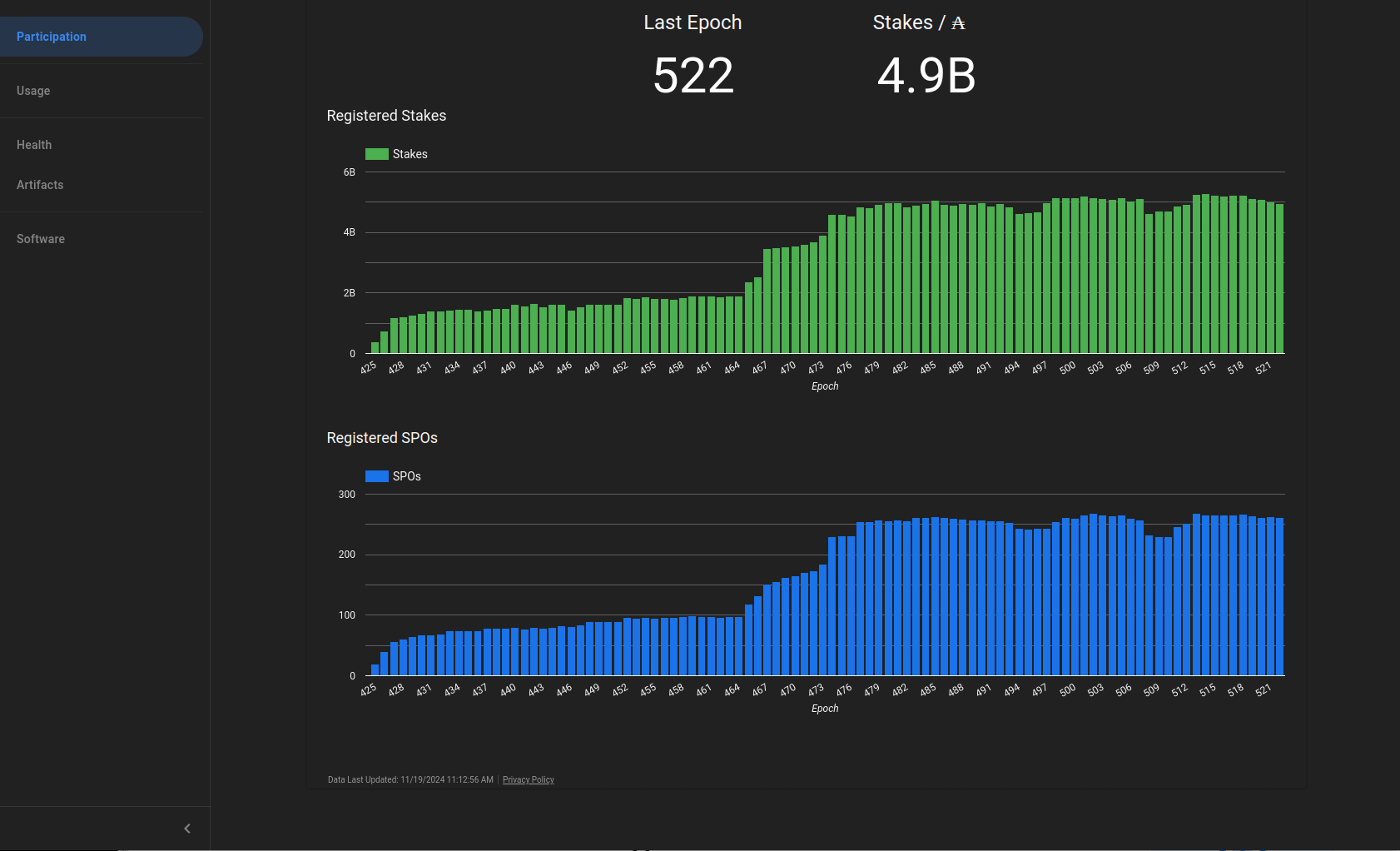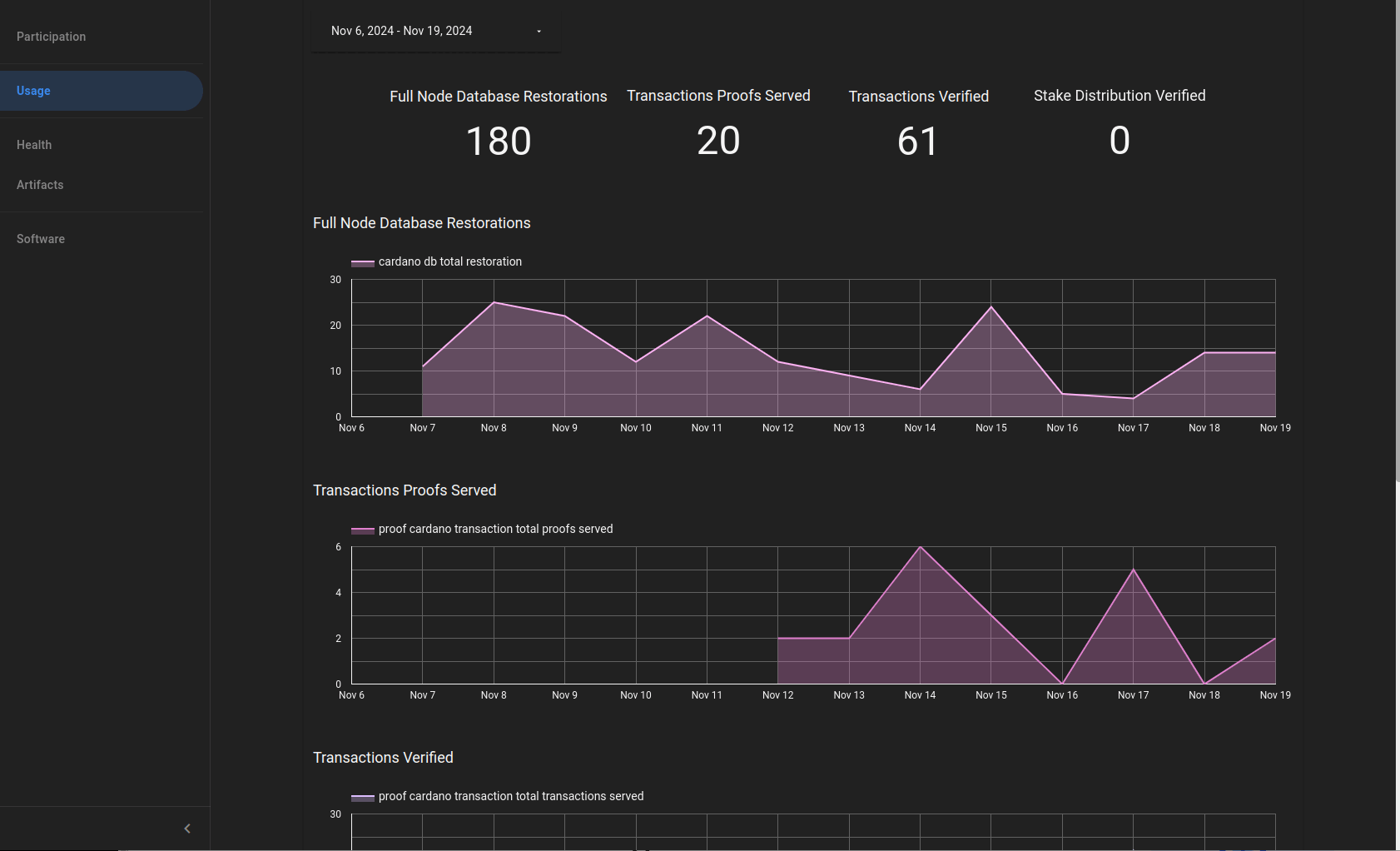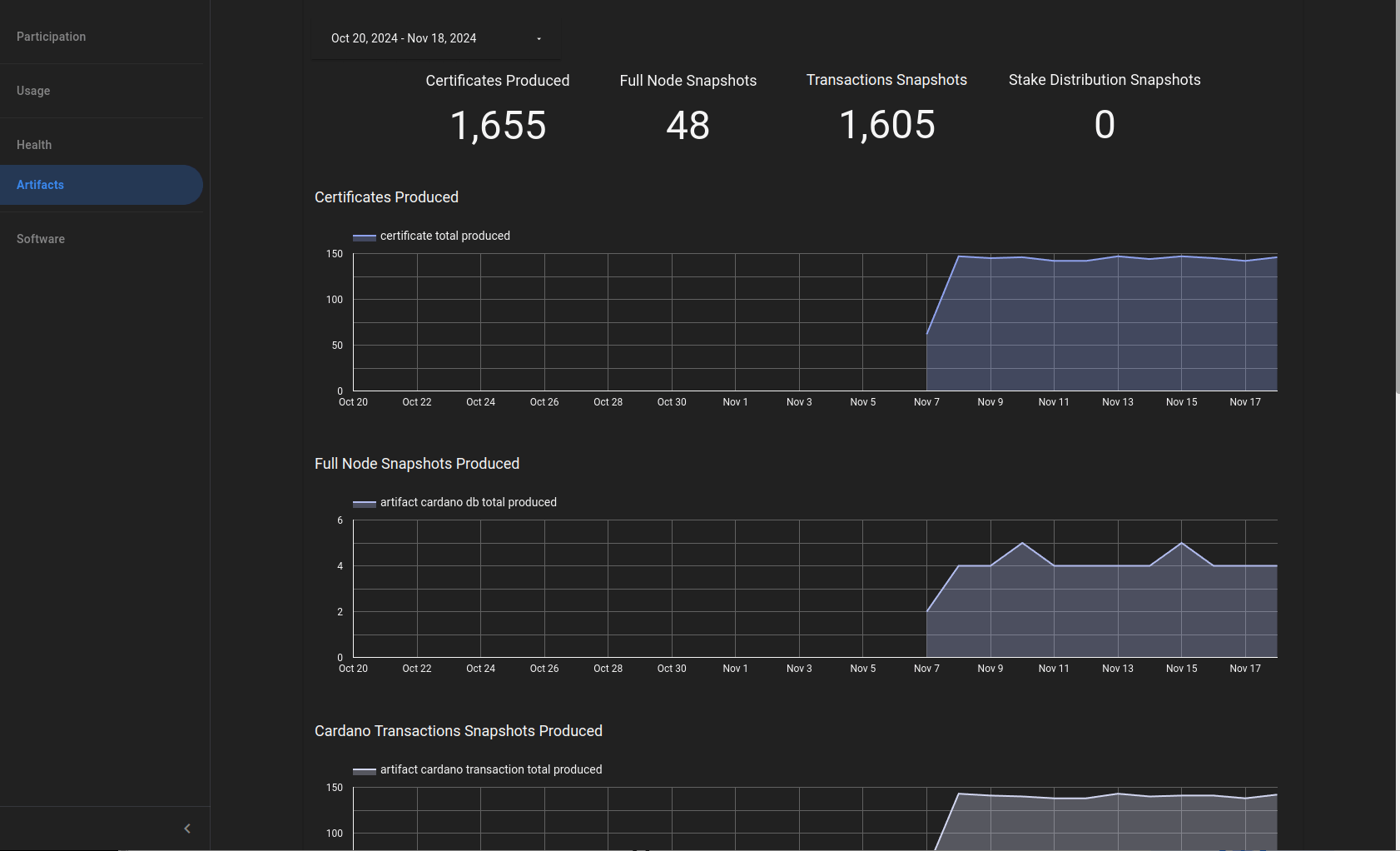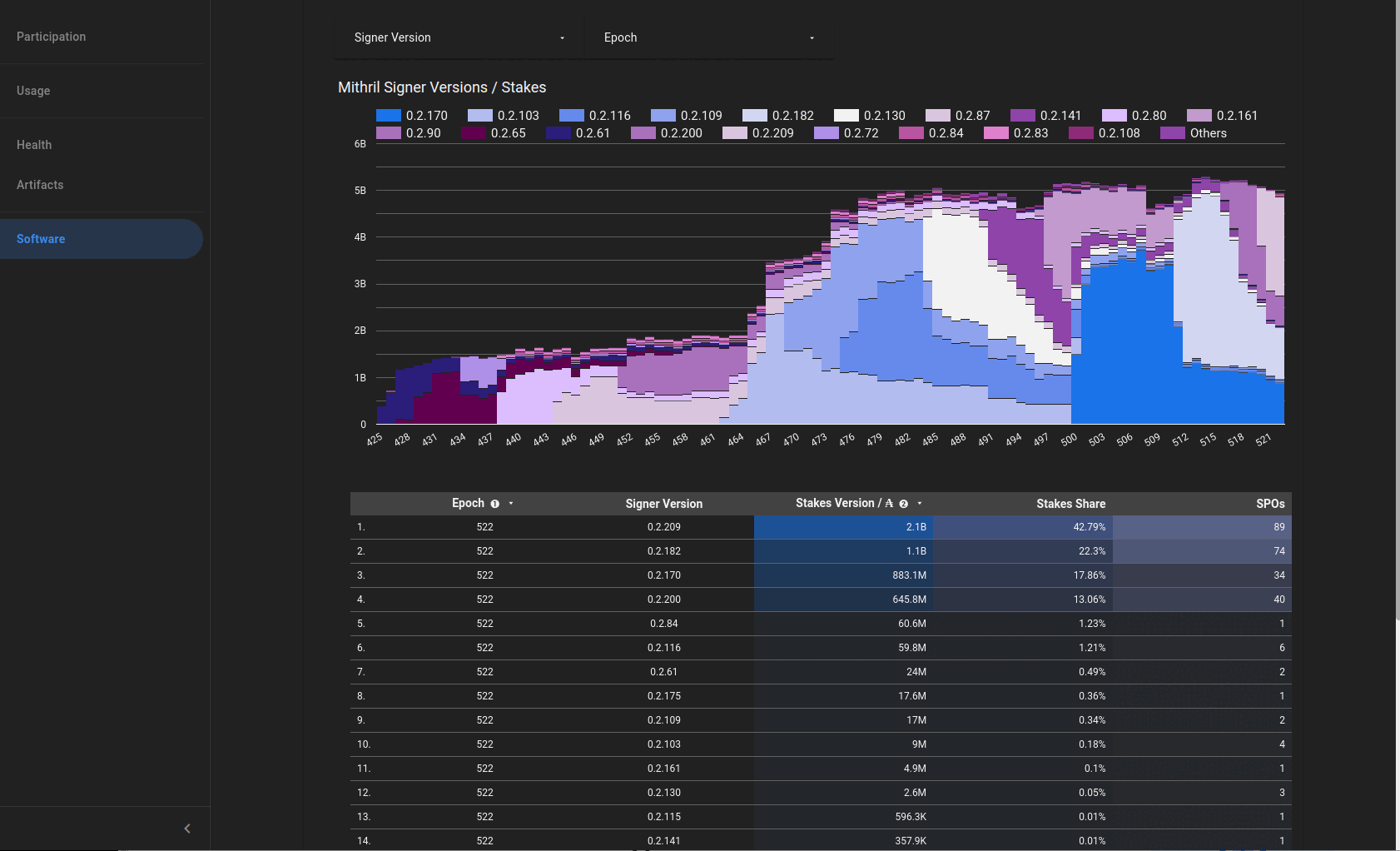
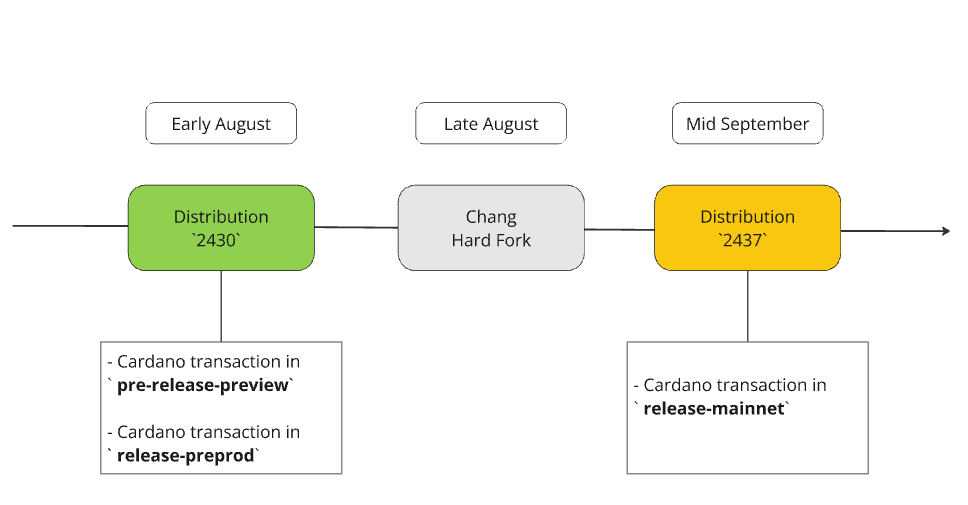
The release-mainnet network has succesfully switched to the Pythagoras era at epoch 539!
The transaction to activate the era switch to Pythagoras has been created on the release-mainnet network at epoch 537.
The era switch will be completed at the transition to epoch 539.
Mithril signer versions compatible with the new Pythagoras era are:
0.2.2210.2.2090.2.200.
All other versions are not compatible with the new era and must be updated.
You can easily update your Mithril signer with this one-line command (it will be downloaded to the current directory by default; you can specify a custom folder with the -p option):
curl --proto '=https' --tlsv1.2 -sSf https://raw.githubusercontent.com/input-output-hk/mithril/refs/heads/main/mithril-install.sh | sh -s -- -c mithril-signer -d latest -p $(pwd)
Era switch plan for Pythagoras
-
pre-release-preview network:
- Create the era switch transaction (done at epoch
757) - Complete the era switch to
Pythagorasat the transition to epoch759
- Create the era switch transaction (done at epoch
-
release-preprod network:
- Create the era switch transaction (done at epoch
184) - Complete the era switch to
Pythagorasat the transition to epoch186
- Create the era switch transaction (done at epoch
-
release-mainnet network:
- Create the era switch transaction (done at epoch
537) - Complete the era switch to
Pythagorasat the transition to epoch539.
- Create the era switch transaction (done at epoch
We use the era switch mechanism to introduce breaking changes in the Mithril protocol. Because these features are not backward compatible with the previous era, at least 95% of the stake must be running the new version for Pythagoras to activate. Refer to the Mithril network upgrade strategy ADR for more details.
For any inquiries or assistance, don't hesitate to contact the team on the Discord channel.